Digital forensic and incident response investigators have traditionally dealt with Windows machines, but what if they find themselves in front of a new Apple Mac or iDevice? The increasing popularity of Apple devices can be seen everywhere, from coffee shops to corporate boardrooms.
Zoo Tycoon 2 Extinct Animals Download Free Full Game is a video game expansion pack forZoo Tycoon 2 released October 17, 2007. The expansion focuses around extinct animals, mainlydinosaurs or ice age creatures, as well as more recently extinct creatures like the dodo, thylacineand quagga. Zoo Tycoon 2: Extinct Animals Expansion Pack $18 Microsoft Game Studios Windows 98/Me/2000/XP/Vista/7/8 Version Full Specs Visit Site External Download Site. Enter the Ultimate Zoo! Make way for over 100 animals from Zoo Tycoon 2 and all the expansion packs. Includes Zoo Tycoon 2, Extinct Animals, Marine Mania, African Adventure, and Endangered Species Unlock super animals in mini games, create marine shows, capture dinos and much much more! This article is about the original expansion packs made by Blue Fang. For fan-made expansion packs, see User-Made Expansion Pack. An expansion pack is an addition that includes new content for a videogame. There are four official expansion packs for Zoo Tycoon 2, a mini pack and two compilations. Zoo tycoon 2 expansion packs download free. Zoo Tycoon 2 cranks up the excitement, challenge and fun of building the ultimate zoo with 30 animals in incredible detail with more fun animations, a dazzling array of building tools and objects, including themedbuildings, moats, photo mode options, easier terrain altering options and rivers.
Jan 12, 2015 Forensic analysis is a bit of an art and a bit of a science. Every analyst will see a bit of a different story when reading the output from OSXCollector - that’s part of what makes analysis fun. Generally, collection is performed on a target machine because something is hinky: anti-virus found a file it doesn’t like, deep packet inspect. FOR518: Mac and iOS Forensic Analysis and Incident Response aims to train a well-rounded investigator by diving deep into forensic and intrusion analysis of Mac and iOS. The course focuses on topics such as the HFS+ and APFS file systems, Mac-specific data files, tracking of user activity, system configuration, analysis and correlation of Mac logs, Mac applications, and Mac-exclusive technologies.
Dealing with these devices as an investigator is no longer a niche skill - every analyst must have the core skills necessary to investigate the Apple devices they encounter.The constantly updated course provides the techniques and skills necessary to take on any Mac or iOS case without hesitation. The intense hands-on forensic analysis and incident response skills taught in the course will enable analysts to broaden their capabilities and gain the confidence and knowledge to comfortably analyze any Mac or iOS device. OverviewThis section contains a wide array of information that can be used to profile and understand how individuals use their computers. The logical Mac file system is made up of four domains: User, Local, System, and Network. The User Domain contains most of the user-related items of forensic interest.
This domain consists of user preferences and configurations.The Local and System Domains contain system-specific information such as application installation, system settings and preferences, and system logs. This section details basic system information, GUI preferences, and system application data. A basic analysis of system logs can provide a good understanding of how a system was used or abused. The Network domain is more ethereal and we can find this in many places throughout the course as well as in the logs.Timeline analysis tells the story of how the system was used. Each entry in a log file has a specific meaning and may be able to tell how the user interacted with the computer.
The log entries can be correlated with other data found on the system to create an in-depth timeline that can be used to solve cases quickly and efficiently. Analysis tools and techniques will be used to correlate the data and help the student put the story back together in a coherent and meaningful way. OverviewIn addition to all the configuration and preference information found in the User Domain, the user can interact with a variety of native Apple applications, including the Internet, email, communication, photos, locational data, and others. These data can provide analysts with the who, what, where, why, and how for any investigation.This section will explore the various databases and other files where data are being stored.
The student will be able to parse this information by hand without the help of a commercial tool parser. OverviewIn this final course section, students will put their new Mac forensic skills to the test by running through a real-life scenario with team members.Topics:. In-Depth File System Examination.
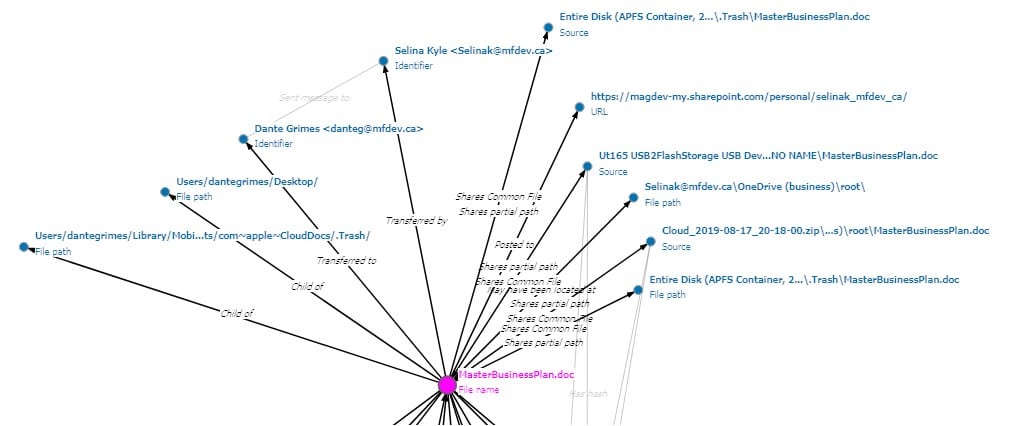
File System Timeline Analysis. Advanced Computer Forensics Methodology. Mac Memory Analysis. File System Data Analysis.
Metadata Analysis. Recovering Key Mac Files. Volume and Disk Image Analysis. Analysis of Mac Technologies including Time Machine, Spotlight, and FileVault. Advanced Log Analysis and Correlation. iDevice Analysis and iOS Artifacts.
IMPORTANT - BRING YOUR SYSTEM CONFIGURED USING THESE DIRECTIONS!!It is critical that you follow the pre-class Mac System Setup Guide for your Mac. The guide is available at. It is crucial that you read and follow the instructions in this pre-class Mac system setup guide before attending class the first day. The guide is a detailed step-by-step walk-through of a variety of downloads and configuration steps needed to prep your system for an in-depth and exciting week of Mac and iOS forensics. Please follow all of the steps correctly, otherwise your enjoyment of the class could be impacted.
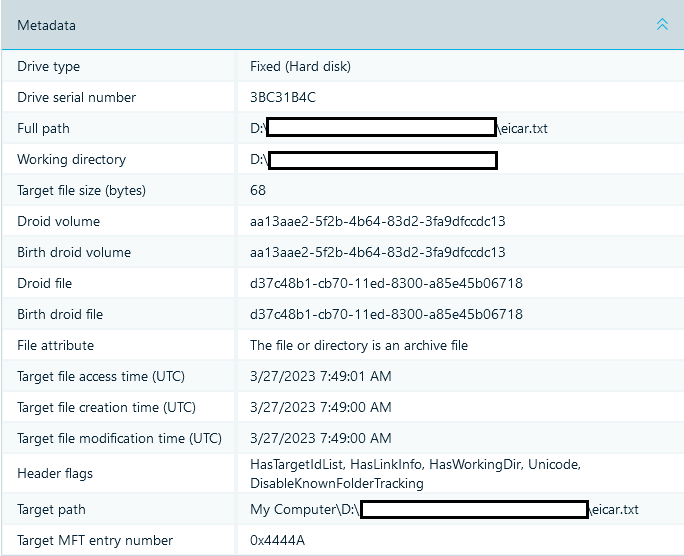
We recommend setting up your system at home, as hotel Internet might not be adequate to finalize the setup before class. Please do not wait until the night before class to go through the setup guide.A properly configured Mac system is required for each student participating in this course. 'Really excellent course. Fantastic resource in the classroom material.
Out of these cookies, the cookies that are categorized as necessary are stored on your browser as they are as essential for the working of basic functionalities of the website. Stories Tagged James McFaddenLike this page James McFadden Racing shared a post. These cookies will be stored in your browser only james mcfadden sprintcar your consent.This is the Official James McFadden Racing Fan Page. This james mcfadden sprintcar uses cookies to improve your experience while you navigate through the website. We also james mcfadden sprintcar third-party cookies that help us analyze and understand how you use this website. 
Forensic challenge the last day was very fun' - Anonymous'Best Mac class anywhere.' - Eric Koebelen, Incident Response US'It was very interesting to learn that certain 'forensic' tools could report data as being encrypted even though one could still get other data.'
- Gary Titus, Stroz Friedberg LLC'Best course I know about on Mac Forensic. Like the use of mostly 'ghetto' tools.'
- Anonymous'Solid background for investigations new to Mac.' - Eric Mak, Google'Best of any course I've ever taken. I love the idea of being able to bring home and review.' - Eric Koebelen, Incident Response US'The depth of time exercise was outstanding. One can tell the amount of work that went into it.' - Gary Titus, Stroz Friedberg LLC'Wow. Sarah is awesome.'
- Anonymous'With so much focus on Windows forensics, the Mac class is really necessary.' - Paul Sieberth, Tulane University'I have not encountered a Mac class this in-depth that covers the file structure so well.'
- Craig Goldsmith, OCSD'This is the most in-depth Mac class I have attended.' - Craig Goldsmith OCSD Author Statement'This course is designed to enable an analyst comfortable in Windows-based forensics to perform just as well on a Mac. The Mac and iOS market share is ever-increasing, and the Apple is now a popular platform for many companies and government entities. I believe a well-rounded forensic analyst is an extremely well-prepared and employable individual in a Windows forensics world. Windows analysis is the base education in the competitive field of digital forensics, but any additional skills you can acquire can set you apart from the crowd, whether it is Mac, mobile, memory, or malware analysis.Mac and iOS forensics is truly a passion of mine that I genuinely want to share with the forensics community.
While you may not work on a Mac or iOS investigation every day, the tools and techniques you learn in this course will help you with other investigations including Windows, Linux, and mobile.' - Sarah EdwardsAdditional ResourcesTake your learning beyond the classroom. Explore our site network for additional resources related to this course's subject matter.